JTAG Debugging
This document provides a guide to installing OpenOCD for ESP32-S2 and debugging using GDB. The document is structured as follows:
- Introduction
Introduction to the purpose of this guide.
- How it Works?
Description how ESP32-S2, JTAG interface, OpenOCD and GDB are interconnected and working together to enable debugging of ESP32-S2.
- Selecting JTAG Adapter
What are the criteria and options to select JTAG adapter hardware.
- Setup of OpenOCD
Procedure to install OpenOCD and verify that it is installed.
- Configuring ESP32-S2 Target
Configuration of OpenOCD software and setting up of JTAG adapter hardware, which together make up the debugging target.
- Launching Debugger
Steps to start up a debug session with GDB from Eclipse and from Command Line.
- Debugging Examples
If you are not familiar with GDB, check this section for debugging examples provided from Eclipse as well as from Command Line.
- Building OpenOCD from Sources
Procedure to build OpenOCD from sources for Windows, Linux and macOS operating systems.
- Tips and Quirks
This section provides collection of tips and quirks related to JTAG debugging of ESP32-S2 with OpenOCD and GDB.
Introduction
Espressif has ported OpenOCD to support the ESP32-S2 processor and the multi-core FreeRTOS (which is the foundation of most ESP32-S2 apps). Additionally, some extra tools have been written to provide extra features that OpenOCD does not support natively.
This document provides a guide to installing OpenOCD for ESP32-S2 and debugging using GDB under Linux, Windows and macOS. Except for OS specific installation procedures, the s/w user interface and use procedures are the same across all supported operating systems.
Note
Screenshots presented in this document have been made for Eclipse Neon 3 running on Ubuntu 16.04 LTS. There may be some small differences in what a particular user interface looks like, depending on whether you are using Windows, macOS or Linux and / or a different release of Eclipse.
How it Works?
The key software and hardware components that perform debugging of ESP32-S2 with OpenOCD over JTAG (Joint Test Action Group) interface is presented in the diagram below under the “Debugging With JTAG” label. These components include xtensa-esp32s2-elf-gdb debugger, OpenOCD on chip debugger, and the JTAG adapter connected to ESP32-S2 target.
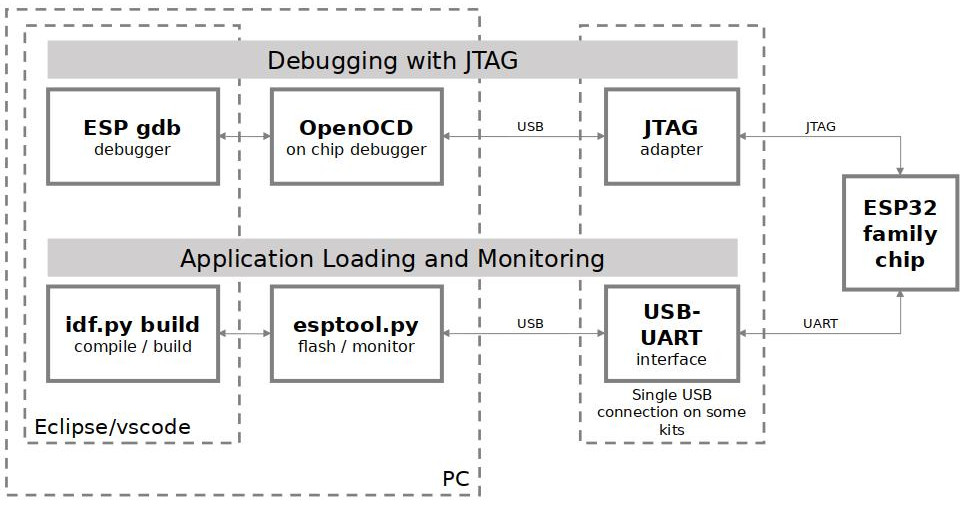
JTAG debugging - overview diagram
Likewise, the “Application Loading and Monitoring” label indicates the key software and hardware components that allow an application to be compiled, built, and flashed to ESP32-S2, as well as to provide means to monitor diagnostic messages from ESP32-S2.
“Debugging With JTAG” and “Application Loading and Monitoring” is integrated under the Eclipse IDE in order to provide a quick and easy transition between writing/compiling/loading/debugging code. The Eclipse IDE (and the integrated debugging software) is available for Windows, Linux and macOS platforms. Depending on user preferences, both the debugger and idf.py build can also be used directly from terminal/command line, instead of Eclipse.
If the ESP32-S2-Kaluga-1 is used, then connection from PC to ESP32-S2 is done effectively with a single USB cable. This is made possible by the FT2232H chip, which provides two USB channels, one for JTAG and the other for UART connection.
Selecting JTAG Adapter
The quickest and most convenient way to start with JTAG debugging is by using ESP32-S2-Kaluga-1. Each version of this development board has JTAG interface already built in. No need for an external JTAG adapter and extra wiring / cable to connect JTAG to ESP32-S2. ESP32-S2-Kaluga-1 is using FT2232H JTAG interface operating at 20 MHz clock speed, which is difficult to achieve with an external adapter.
If you decide to use separate JTAG adapter, look for one that is compatible with both the voltage levels on the ESP32-S2 as well as with the OpenOCD software. The JTAG port on the ESP32-S2 is an industry-standard JTAG port which lacks (and does not need) the TRST pin. The JTAG I/O pins all are powered from the VDD_3P3_RTC pin (which normally would be powered by a 3.3 V rail) so the JTAG adapter needs to be able to work with JTAG pins in that voltage range.
On the software side, OpenOCD supports a fair amount of JTAG adapters. See https://openocd.org/doc/html/Debug-Adapter-Hardware.html for an (unfortunately slightly incomplete) list of the adapters OpenOCD works with. This page lists SWD-compatible adapters as well; take note that the ESP32-S2 does not support SWD. JTAG adapters that are hardcoded to a specific product line, e.g. ST-LINK debugging adapters for STM32 families, will not work.
The minimal signalling to get a working JTAG connection are TDI, TDO, TCK, TMS and GND. Some JTAG debuggers also need a connection from the ESP32-S2 power line to a line called e.g. Vtar to set the working voltage. SRST can optionally be connected to the CH_PD of the ESP32-S2, although for now, support in OpenOCD for that line is pretty minimal.
ESP-Prog is an example for using an external board for debugging by connecting it to the JTAG pins of ESP32-S2.
Setup of OpenOCD
If you have already set up ESP-IDF with CMake build system according to the Getting Started Guide, then OpenOCD is already installed. After setting up the environment in your terminal, you should be able to run OpenOCD. Check this by executing the following command:
openocd --version
The output should be as follows (although the version may be more recent than listed here):
Open On-Chip Debugger v0.10.0-esp32-20190708 (2019-07-08-11:04)
Licensed under GNU GPL v2
For bug reports, read
https://openocd.org/doc/doxygen/bugs.html
You may also verify that OpenOCD knows where its configuration scripts are located by printing the value of OPENOCD_SCRIPTS environment variable, by typing echo $OPENOCD_SCRIPTS (for Linux and macOS) or echo %OPENOCD_SCRIPTS% (for Windows). If a valid path is printed, then OpenOCD is set up correctly.
If any of these steps do not work, please go back to the setting up the tools section of the Getting Started Guide.
Note
It is also possible to build OpenOCD from source. Please refer to Building OpenOCD from Sources section for details.
Configuring ESP32-S2 Target
Once OpenOCD is installed, you can proceed to configuring the ESP32-S2 target (i.e ESP32-S2 board with JTAG interface). Configuring the target is split into the following three steps:
Configure and connect JTAG interface
This step depends on the JTAG and ESP32-S2 board you are using (see the two cases described below).
Run OpenOCD
Once target is configured and connected to computer, you are ready to launch OpenOCD.
Open a terminal and set it up for using the ESP-IDF as described in the setting up the environment section of the Getting Started Guide. Then run OpenOCD (this command works on Windows, Linux, and macOS):
openocd -f board/esp32s2-kaluga-1.cfg
Note
The files provided after -f above are specific for ESP32-S2-Kaluga-1 board. You may need to provide different files depending on the hardware that is used. For guidance see Configuration of OpenOCD for specific target.
For example, board/esp32c3-ftdi.cfg can be used for a custom board with an FT2232H or FT232H chip used for JTAG connection, or with ESP-Prog.
You should now see similar output (this log is for ESP32-S2-Kaluga-1 board):
user-name@computer-name:~/esp/esp-idf$ openocd -f board/esp32s2-kaluga-1.cfg
Open On-Chip Debugger v0.10.0-esp32-20200420 (2020-04-20-16:15)
Licensed under GNU GPL v2
For bug reports, read
https://openocd.org/doc/doxygen/bugs.html
none separate
adapter speed: 20000 kHz
force hard breakpoints
Info : ftdi: if you experience problems at higher adapter clocks, try the command "ftdi_tdo_sample_edge falling"
Info : clock speed 20000 kHz
Info : JTAG tap: esp32s2.cpu0 tap/device found: 0x120034e5 (mfg: 0x272 (Tensilica), part: 0x2003, ver: 0x1)
Info : esp32s2: Debug controller was reset (pwrstat=0x5F, after clear 0x0F).
Info : esp32s2: Core was reset (pwrstat=0x5F, after clear 0x0F).
If there is an error indicating permission problems, please see section on “Permissions delegation” in the OpenOCD README file located in the
~/esp/openocd-esp32directory.In case there is an error in finding the configuration files, e.g.
Can't find board/esp32s2-kaluga-1.cfg, check if theOPENOCD_SCRIPTSenvironment variable is set correctly. This variable is used by OpenOCD to look for the files specified after the-foption. See Setup of OpenOCD section for details. Also check if the file is indeed under the provided path.If you see JTAG errors (e.g.,
...all onesor...all zeroes), please check your JTAG connections, whether other signals are connected to JTAG besides ESP32-S2’s pins, and see if everything is powered on correctly.
Upload application for debugging
Build and upload your application to ESP32-S2 as usual, see Step 5. First Steps on ESP-IDF.
Another option is to write application image to flash using OpenOCD via JTAG with commands like this:
openocd -f board/esp32s2-kaluga-1.cfg -c "program_esp filename.bin 0x10000 verify exit"
OpenOCD flashing command program_esp has the following format:
program_esp <image_file> <offset> [verify] [reset] [exit]
image_file- Path to program image file.
offset- Offset in flash bank to write image.
verify- Optional. Verify flash contents after writing.
reset- Optional. Reset target after programing.
exit- Optional. Finally exit OpenOCD.
compress- Optional. Compress image file before programming.
encrypt- Optional. Encrypt binary before writing to flash. Same functionality withidf.py encrypted-flash
no_clock_boost- Optional. Disable setting target clock frequency to its maximum possible value before programming. Clock boost is enabled by default.
restore_clock- Optional. Restore clock frequency to its initial value after programming. Disabled by default.
You are now ready to start application debugging. Follow the steps described in the section below.
Launching Debugger
The toolchain for ESP32-S2 features GNU Debugger, in short GDB. It is available with other toolchain programs under filename: xtensa-esp32s2-elf-gdb. GDB can be called and operated directly from command line in a terminal. Another option is to call it from within IDE (like Eclipse, Visual Studio Code, etc.) and operate indirectly with help of GUI instead of typing commands in a terminal.
Both options of using debugger are discussed under links below.
It is recommended to first check if debugger works from Command Line and then move to using Eclipse.
Debugging Examples
This section is intended for users not familiar with GDB. It presents example debugging session from Eclipse using simple application available under get-started/blink and covers the following debugging actions:
Similar debugging actions are provided using GDB from Command Line.
Before proceeding to examples, set up your ESP32-S2 target and load it with get-started/blink.
Building OpenOCD from Sources
Please refer to separate documents listed below, that describe build process.
The examples of invoking OpenOCD in this document assume using pre-built binary distribution described in section Setup of OpenOCD.
To use binaries build locally from sources, change the path to OpenOCD executable to src/openocd and set the OPENOCD_SCRIPTS environment variable so that OpenOCD can find the configuration files. For Linux and macOS:
cd ~/esp/openocd-esp32
export OPENOCD_SCRIPTS=$PWD/tcl
For Windows:
cd %USERPROFILE%\esp\openocd-esp32
set "OPENOCD_SCRIPTS=%CD%\tcl"
Example of invoking OpenOCD build locally from sources, for Linux and macOS:
src/openocd -f board/esp32s2-kaluga-1.cfg
and Windows:
src\openocd -f board/esp32s2-kaluga-1.cfg
Tips and Quirks
This section provides collection of links to all tips and quirks referred to from various parts of this guide.
- Tips and Quirks
- Breakpoints and watchpoints available
- What else should I know about breakpoints?
- Flash Mappings vs SW Flash Breakpoints
- Why stepping with “next” does not bypass subroutine calls?
- Support options for OpenOCD at compile time
- FreeRTOS support
- Optimize JTAG speed
- What is the meaning of debugger’s startup commands?
- Configuration of OpenOCD for specific target
- How debugger resets ESP32-S2?
- Do not use JTAG pins for something else
- JTAG with Flash Encryption or Secure Boot
- Reporting issues with OpenOCD / GDB